Website Spoofing in 2026: How to Detect and Take Down Fake Sites
Website spoofing has evolved from crude knockoffs to sophisticated digital replicas that steal revenue, damage trust, and hijack customer journeys. In 2026, generative AI and automated phishing kits make it easier than ever to spin up fake versions of legitimate websites, often within minutes. These impersonator sites are designed to deceive—with branding, product listings, user flows, and even checkout experiences that mimic the real thing.
Spoofing isn’t just a cybersecurity issue – it’s a brand crisis. The longer a spoofed site stays live, the more damage it inflicts on your revenue, reputation, and SEO footprint. And the truth is: the bigger your digital presence, the more likely you’re being spoofed right now.
This guide explains how spoofing works, what modern threats look like, how to detect them in real time, and what steps brands can take to remove spoofed sites quickly and at scale.
What Is Website Spoofing?
Website spoofing is the act of creating a deceptive version of a legitimate website, with the goal of tricking users into believing they’re interacting with an official brand. These sites copy logos, design layouts, product information, and even domain formats.
Common outcomes include:
-
Theft of login credentials or payment details
-
Malware installation on visitor devices
-
Diversion of legitimate traffic and transactions
-
SEO dilution from duplicate or malicious content
-
Long-term brand trust erosion
Spoofing can be standalone or part of a broader phishing campaign. Some spoofed websites are shared through email or SMS. Others are pushed through paid search ads, fake social accounts, or QR codes in the physical world.
How Website Spoofing Works
1. Domain Manipulation
Attackers register domains that resemble your brand. Common tactics include:
-
Typosquatting: replacing letters (e.g., brandsh1eld.com)
-
Homoglyphs: using visually similar characters (e.g., rn instead of m)
-
TLD switching: changing .com to .net, .org, or regional domains
-
Hyphenation or subdomains: brand-shield.com or login.brandshield-security.com
2. Website Cloning
They replicate your site’s HTML, CSS, and visual elements using scraping tools or site copier software. This results in near-identical pages that fool users at a glance.
3. Traffic Engineering
Spoof sites are promoted using:
-
Phishing emails and fake SMS alerts
-
Social media impersonation
-
Paid ads on search engines and social platforms
-
Black-hat SEO tactics to rank in organic results
-
QR code redirects in physical locations
4. Data Harvesting or Malware Injection
The final step depends on the attacker’s goal:
-
Fake login forms to steal credentials
-
Fake checkout to capture credit card data
-
Malware downloads disguised as PDFs or invoices
-
Redirection to affiliate or competitor links
Technical Mechanisms Behind Spoofing Attacks
DNS Spoofing
Attackers compromise DNS entries to reroute legitimate traffic to a malicious site. This is also known as DNS cache poisoning.
Mitigation:
-
Use DNSSEC to validate DNS responses
-
Harden DNS servers to block unauthorized updates
ARP Spoofing
Fraudsters send forged ARP responses to divert internal traffic to malicious machines.
Mitigation:
-
Enable Dynamic ARP Inspection on switches
-
Use static ARP tables in sensitive environments
SSL Exploitation
Spoof sites may use free SSL certificates to appear legitimate. While HTTPS is a baseline, it’s no longer a sign of trust.
Mitigation:
-
Educate users to verify URLs, not just the padlock icon
-
Monitor for unauthorized certificates referencing your brand
The 2026 Threat Landscape: What’s Changed?
AI-Generated Clone Sites
Large language models and design AI tools now allow attackers to create polished spoof websites complete with:
-
Auto-written copy using your tone and brand style
-
Generated product images or avatars
-
Dynamic chatbots that mimic real customer service scripts
Scale of Attacks
-
Over 1.4 million spoof domains were identified globally in 2025
-
Spoofing is now the #1 source of digital fraud loss for consumer-facing brands
-
62% of consumers say they would stop buying from a brand after falling for a spoofed version
Blended Attacks
Spoofing is often paired with phishing, vishing, deepfakes, and impersonation to create full-spectrum fraud campaigns. A single fake website may be supported by:
-
Social media DMs
-
Fake email alerts
-
QR codes
-
AI voice bots
Real‑World Examples of Website Spoofing
Banking and Financial Services
In the banking sector, website spoofing is often tied to urgency‑driven fraud. Attackers clone online banking portals for regional and national banks, copying login screens, two‑factor authentication prompts, and security banners. Victims are typically redirected to these sites through fake fraud alerts sent by email or SMS, warning of “suspicious activity” that requires immediate action. Once users enter their credentials or one‑time passcodes, attackers can initiate real transactions on the legitimate banking platform. These attacks are particularly damaging because they erode customer confidence in digital banking channels and frequently lead to regulatory scrutiny and mandatory incident disclosures.
E‑Commerce and Retail Brands
E‑commerce brands are prime targets for website spoofing due to high transaction volume and consumer trust. Spoofed retail websites often advertise steep discounts, limited‑time sales, or exclusive product drops that mimic real promotions. Some of these sites exist purely to steal payment information, while others sell counterfeit goods under the guise of a legitimate brand. In both cases, customers blame the brand when orders never arrive or products fail to match expectations. Beyond immediate fraud losses, these spoofed sites can harm SEO performance by duplicating product pages and siphoning branded search traffic away from the official website.
Pharmaceutical and Healthcare Companies
Website spoofing in the pharmaceutical space carries serious safety and compliance risks. Fraudsters create lookalike websites that promote unapproved treatments, counterfeit prescription drugs, or fake weight‑loss and GLP‑1 medications. These sites often impersonate licensed pharmacies or healthcare providers, complete with copied regulatory language and trust badges. Customers may unknowingly purchase unsafe products or share sensitive health information. For pharmaceutical brands, the impact extends beyond brand damage to potential legal exposure, regulatory investigations, and public health consequences if counterfeit medications cause harm.
Cryptocurrency and Digital Asset Platforms
Cryptocurrency platforms are frequently targeted by highly sophisticated website spoofing campaigns. Attackers build pixel‑perfect replicas of crypto exchanges, wallet providers, or DeFi platforms, often paired with phishing emails or fake social media announcements. Victims are prompted to “verify” their wallet, reconnect accounts, or resolve a fabricated security issue. Once users enter seed phrases or private keys, attackers drain funds almost instantly. Unlike traditional fraud, crypto theft is often irreversible, making these spoofing attacks especially devastating for both users and the brands whose names are abused in the process.
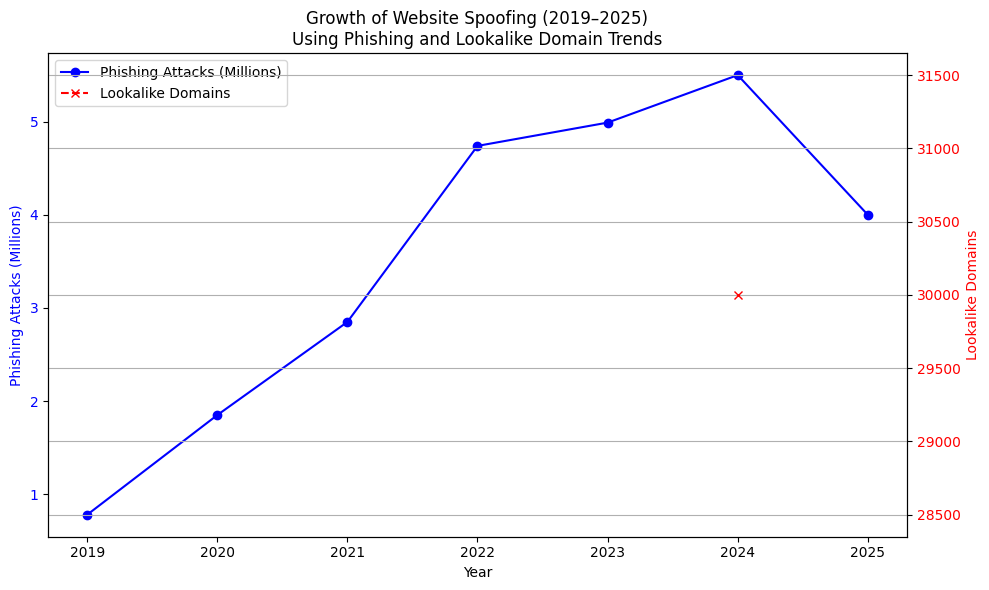
From 2019 through 2023, reported phishing attacks climbed steeply from under one million annual incidents to nearly five million per year, reflecting a ~6× increase in just three years—mirroring the growth in deceptive website deployment often used to harvest credentials and impersonate brands online. In 2024, security researchers identified over 30,000 impersonation domains targeting major global brands, underlining the expanding scale of lookalike URL abuse.
In 2025, quarterly phishing activity continued at historically high levels, with over one million attacks recorded in early 2025—the highest quarterly volume observed since late 2023—indicating that spoofing and credential‑harvesting sites remain a persistent threat.
How to Detect Website Spoofing Before Damage Spreads
1. Monitor Lookalike Domains
Use automated scanners to detect new domains that resemble your brand:
-
Misspellings
-
Similar characters
-
Suspicious subdomains
-
Internationalized domain names (IDNs)
2. Use AI-Based Threat Clustering
Spoofing rarely occurs in isolation. AI-based systems like BrandShield’s AI.ClusterX group together suspicious domains, social handles, and ad campaigns into threat clusters—enabling faster detection and context.
3. Monitor Referral Traffic and Brand Mentions
Sudden spikes in traffic from unknown sources—or drops in conversion rates—may point to spoofing. Set up alerts for brand mentions and URL indexing across search engines.
4. Scan the Dark Web and Fraud Markets
Spoofed domains are often shared or sold before launch. Monitoring forums and private Telegram groups gives early warning of active campaigns.
How to Prevent Website Spoofing
1. Register Defensive Domains
Secure common misspellings, alternate TLDs, and brand + category combinations. Block attackers before they can use them.
2. Configure Your Infrastructure
-
Enforce HTTPS with HSTS
-
Set up SPF, DKIM, and DMARC to protect email authenticity
-
Use certificate transparency logs to track SSL issues
3. Deploy Automated Enforcement
Manual takedowns don’t scale. Use enforcement platforms that automatically:
-
Gather legal evidence
-
Submit registrar/host takedown requests
-
Follow up and escalate when needed
4. Establish Internal Protocols
Create an SOP for spoofing events:
-
Who gets notified (IT, legal, PR)
-
What evidence is gathered
-
How customers are informed if needed
What to Do If You Discover a Spoofed Website
-
Document it: Capture screenshots, headers, WHOIS, and URLs
-
Submit takedown requests: Registrar, host, domain provider
-
Escalate through a provider like BrandShield if no response
-
Communicate internally: Align security, marketing, legal
-
Notify customers: If exposure is likely, issue guidance through owned channels
-
Track for recurrence: Once spoofed, brands are often targeted again
SEO Risks of Website Spoofing
-
Duplicate content may harm your site’s ranking
-
Fraudulent backlinks from spoofed domains can result in penalties
-
Customers misled by fake Google results may bounce from your actual site
-
Paid ads may lose efficiency due to click diversion or confusion
BrandShield’s Approach to Website Spoofing
-
AI.ClusterX™ groups fake domains, social accounts, and ads into unified threat clusters
-
Automated Takedowns: Rapid enforcement across domains, marketplaces, social, and app stores
-
Real-Time Alerts: Your team is notified the moment threats appear
-
Full-Service Support: Our enforcement analysts handle the manual work
Website Spoofing Checklist for Brands
-
Register key domain variations (typos, TLDs, etc.)
-
Enable 24/7 domain and brand monitoring
-
Implement DMARC, SPF, and DKIM
-
Use HTTPS with valid SSL across all properties
-
Establish internal SOPs for enforcement and escalation
-
Partner with a dedicated brand protection platform such as BrandShield
FAQs
How do I know if my brand is being spoofed?
Start with domain monitoring. Look for traffic anomalies, phishing complaints, or duplicate content alerts.
Is spoofing the same as phishing?
No. Spoofing is the infrastructure (fake site), phishing is the delivery method (email/SMS/social).
Can spoofed websites show up in search results?
Yes. If left unchecked, spoofed sites can rank using black-hat SEO tactics and even bid on your brand keywords.
Is spoofing illegal?
Yes. It violates copyright, trademark, and fraud laws in most jurisdictions. Legal action is possible when paired with proper evidence.
What’s the fastest way to remove a spoofed site?
Use an automated enforcement platform like BrandShield that works directly with registrars and hosts.
Final Thoughts: Don’t Let Fake Sites Steal Your Brand
Website spoofing is not just a scam. It’s an attack on your reputation, revenue, and customer relationships. Brands that act quickly—and intelligently—can drastically reduce the impact.
BrandShield helps you monitor, detect, and take down spoofed websites at scale, using AI, automation, and real-time enforcement. Let us show you the threats already targeting your brand.
→ Schedule your free threat assessment with BrandShield.